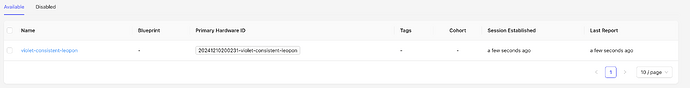
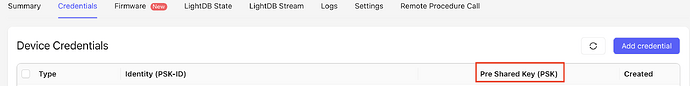
Hi,
I’m trying to run the hello_nrf91_offloaded sample on a Thingy91X and am running into the following error:
[00:08:00.827,972] <err> golioth_coap_client_zephyr: Failed to connect to socket: -116
[00:08:00.828,369] <err> golioth_coap_client_zephyr: Failed to connect: -116
[00:08:00.828,369] <wrn> golioth_coap_client_zephyr: Failed to connect: -116
I built and flashed the application using the following invocations:
$> west build -p -b thingy91x/nrf9151/ns hello_nrf91_offloaded/
$> west --recover flash
I loaded my Golioth PSK using the AT commands in the README and confirmed that it is loaded:
uart:~$ nrf_modem_at AT%CMNG=1
%CMNG: 1001,0,"5D550643B6400D4341550A9B14AEDD0B4FAC33AE5DEB7D8247B6B4F799C13306"
%CMNG: 1002,0,"2C43952EE9E000FF2ACC4E2ED0897C0A72AD5FA72C3D934E81741CBD54F05BD1"
%CMNG: 1003,0,"39FDCF28AEFFE08D03251FCCAF645E3C5DE19FA4EBBAFC89B4EDE2A422148BAB"
%CMNG: 4242,0,"9773A4830889B5C1052796CDB00962A5C65C087D06ADBF59752AFE7AE0BB6F42"
%CMNG: 4242,1,"8B1E3EB816B23FD9505EE8F155B3A6063EF9CB6C7BDC0C6743CE205180589D13"
%CMNG: 4242,2,"D0FCA5D6B82CD435FEBE011E35978CA5B9BD71943F06C30885B40A6C45CAF4B0"
%CMNG: 515765868,3,"3039B585A436A75BA8BB6C774B9DCEA8B3102E9E56CFDADCB6409870DEF41282"
%CMNG: 515765868,4,"7D69C98E1F0B7C77BF808ACE59147A76FB05EBA20BD52BE6E20FAC43A79E5D7C"
%CMNG: 2147483667,0,"9773A4830889B5C1052796CDB00962A5C65C087D06ADBF59752AFE7AE0BB6F42"
%CMNG: 4294967292,11,"672E2F05962B4EFBFA8801255D87E0E0418F2DDF4DDAEFC59E9B4162F512CB63"
%CMNG: 4294967293,10,"2C43952EE9E000FF2ACC4E2ED0897C0A72AD5FA72C3D934E81741CBD54F05BD1"
%CMNG: 4294967294,6,"61535241D4D0F099C86961DD0D57DDE53F4E0C51959D6BAB13062714B45D8B4D"
OK
I confirmed that I can ping coap.golioth.io using NRF’s modem_shell sample:
mosh:~$ ping -d coap.golioth.io -c 5
Initiating ping to: coap.golioth.io
Source IP addr: 100.117.2.48
Destination IP addr: 34.135.90.112
Modem domain event: CE-level 0
Modem domain event: CE-level 1
RRC mode: Connected
Pinging coap.golioth.io results: no response in given timeout 3000 msec
Pinging coap.golioth.io results: time=0.446secs, payload sent: 0, payload received 0
Pinging coap.golioth.io results: time=0.392secs, payload sent: 0, payload received 0
Pinging coap.golioth.io results: time=0.412secs, payload sent: 0, payload received 0
Pinging coap.golioth.io results: time=1.681secs, payload sent: 0, payload received 0